Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Configurable Metadata Extraction in ASN
From this page, you can enable or disable the following metadata extraction options on the Aviz Service Node (ASN) for 5G-NSA:
IMSI (International Mobile Subscriber Identity): A unique identifier for a mobile subscriber.
IMEI (International Mobile Equipment Identity): A unique identifier for a mobile device.
MSISDN (Mobile Station International Subscriber Directory Number): The phone number associated with the subscriber.
CGI (Cell Global Identifier): A unique identifier for a cell in a mobile network.
SAI (Service Area Identifier): Identifies the service area within a network.
RAI (Routing Area Identifier): Specifies the routing area within a mobile network.
IPv4 Address Uplink (SGW): The IPv4 address for the uplink from the Serving Gateway (SGW).
IPv4 Address Downlink (eNodeB): The IPv4 address for the downlink to the eNodeB (Evolved Node B).
IPv6 Address Uplink (SGW): The IPv6 address for the uplink from the Serving Gateway (SGW).
Cplane Latency: The latency in the control plane, measuring the delay in signaling and control messages.
Per IMSI Metrics:
Uplane Bandwidth/Throughput: The bandwidth or throughput in the user plane, specific to each IMSI .
USER TYPE: Classification of the user, typically indicating subscriber type or service level.
UE IP ADDR(User Equipment IP Address):The IP address assigned to the user's device.
TAI (Tracking Area Identifier): Identifies the tracking area in LTE networks.
ECGI (EUTRAN CGI): A unique identifier for cells in LTE networks.
LAI (Local Area Identifier): Identifies the local area within a GSM network.
Macro eNodeB Field: Information related to the macro eNodeB, a type of base station in LTE networks.
Extended Macro eNodeB Field: Additional information for extended macro eNodeB configurations.
Cell Changed: Indicates whether the user's device has changed cells within the network.
IPv6 Address Downlink (eNodeB): The IPv6 address for the downlink to the eNodeB (Evolved Node B).
TEID Uplink (SGW): The Tunnel Endpoint Identifier for the uplink from the Serving Gateway (SGW).
TEID Downlink (eNodeB): The Tunnel Endpoint Identifier for the downlink to the eNodeB (Evolved Node B).
CONTROL TEID: The Tunnel Endpoint Identifier used for control plane signaling.
CONTROL IP: The IP address used for control plane signaling.
Radio Access Type (RAT): The type of radio access technology being used (e.g., LTE, 5G).
Uplane Latency: The latency in the user plane, measuring the delay in data transmission for each IMSI.

The following Metadata Attributes can be modified using this menu:
Radius
Configurable Metadata Extraction in ASN
From this page, you can enable or disable the following metadata extraction options on the Aviz Service Node (ASN) for 5G-SA:
IMSI (International Mobile Subscriber Identity): A unique identifier for a mobile subscriber.
IMEI (International Mobile Equipment Identity): A unique identifier for a mobile device.
MSISDN (Mobile Station International Subscriber Directory Number): The phone number associated with the subscriber.
CGI (Cell Global Identifier): Unique identifier for a cell in a mobile network.
TAI (Tracking Area Identifier): Identifier for tracking areas in a 5G network.
Cell Changed: Indicates whether the user's device has changed cells within the network.
IPV4 Address Uplink (UPF): IPv4 address for the uplink from the User Plane Function (UPF).
IPv4 Address Downlink (RAN): IPv4 address for the downlink to the Radio Access Network (RAN).
IPv6 Address Uplink (UPF): IPv6 address for the uplink from the User Plane Function (UPF).
Cplane Latency: The latency in the control plane, measuring the delay in signaling and control messages.
Per IMSI Metrics:
Uplane Bandwidth/Throughput: Bandwidth or throughput in the user plane for each IMSI.
USER TYPE: Classification of the user, typically indicating subscriber type or service level.
5G-SA TYPE: Type of 5G network architecture, such as standalone (SA) or non-standalone (NSA).
UE IP ADDR(User Equipment IP Address):The IP address assigned to the user's device.
IPv6 Address Downlink (RAN): IPv6 address for the downlink to the Radio Access Network (RAN).
TEID Uplink (UPF): Tunnel Endpoint Identifier for the uplink from the User Plane Function (UPF).
TEID Downlink (RAN): Tunnel Endpoint Identifier for the downlink to the Radio Access Network (RAN).
RAT (Radio Access Type): The type of radio access technology used, such as 5G NR.
Uplane Latency: Latency in the user plane, measuring data transmission delay for each IMSI.

The list below specifies the unique unified data type of metadata attributes exported from ASN, 5GC-control-session-data-mapping, EPC-control-session-data-mapping, and the user-session-data-mapping file.
SIP-session-data-mapping
Radius-session-data-mapping
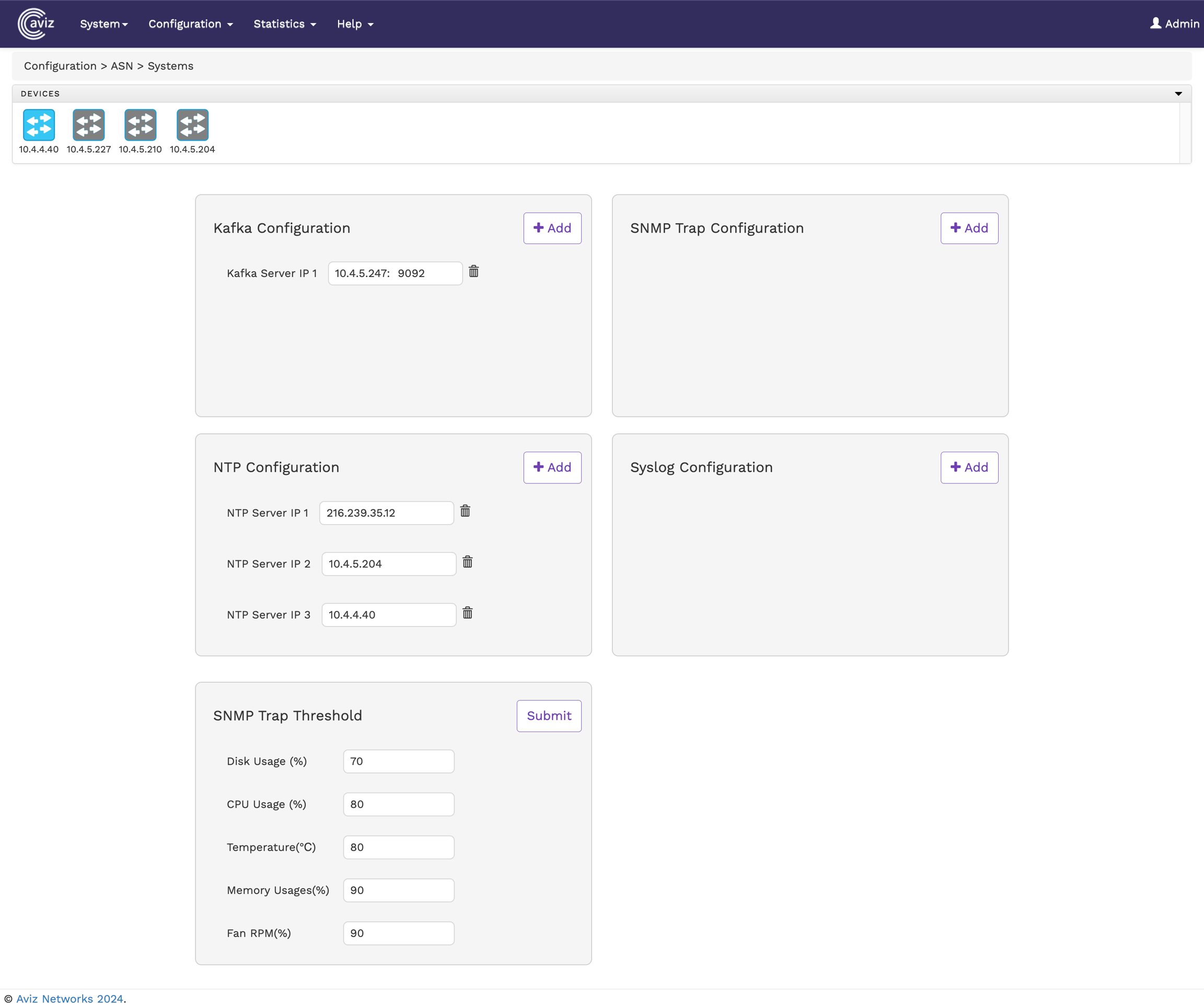
To configure and manage system attributes of ASN via the FlowVision GUI, navigate to:
Configuration > Systems.
The Systems Manager page displays the configurations for Kafka, SNMP, NTP, and Syslog servers, allowing users to add or remove associated IP addresses as needed.
The following image shows the System Parameters page:
Configure and manage up to one Kafka server IP address for exporting metadata extracted by the Service Node.
Configure and manage up to three SNMP trap server IP addresses for receiving SNMP traps generated by the Service Node.
Configure and manage up to three NTP server IP addresses for time synchronization.
Configure and manage up to three Syslog server IP addresses for receiving system logs from the Service Node.
Set thresholds for SNMP traps based on the following parameters:
Disk Usage (%): Define a trigger when disk utilization exceeds a specified percentage.
CPU Usage (%): Set a threshold for CPU utilization percentage.
Temperature (℃): Configure the ASN appliance temperature limit before an SNMP trap is triggered.
FAN RPM (%): Set a limit for fan speed in Revolutions Per Minute (RPM).
To configure Boot Configuration using the FlowVision GUI, navigate to:
Configuration > Boot Configuration.
The following image illustrate the General configs such as hash table, ip & subscriber session limit, Coutn etc as shown below
LB Hash Type:
Specifies the method used for load balancing packet flows across processing cores.
3 Tuples: Uses source IP, destination IP, and protocol/port for hashing.
5 Tuples: Uses source IP, destination IP, protocol, source port, and destination port for hashing.
IP Session Limits:
Sets the maximum number of concurrent IP sessions per core.
Subscriber Session Limits:
Definition: Defines the maximum number of subscriber sessions (unique users/devices) that can be handled simultaneously.
The range is typically 100 to 3,000,000. Higher values require more memory and CPU resources.
Kafka Core Count:
Definition: Number of CPU cores dedicated to Kafka producer threads for exporting data.
Limitation: Must be less than or equal to the number of Packet Processing cores.
KPI Core Count:
Definition: Number of CPU cores allocated for Key Performance Indicator (KPI) processing tasks.
Limitation: Must be less than or equal to the number of Packet Processing cores.
Start Cores:
Definition: Specifies the logical core ID from which packet processing should begin.
Limitation: Must be a valid core ID present on the system. Incorrect values may prevent the application from starting.
Total Cores:
Definition: Total number of logical CPU cores allocated for packet processing and related tasks.
Limitation: Limited by the physical hardware; allocating more cores than available will result in errors.
Packet Processing Cores (Per Port)
Definition: Number of CPU cores assigned to process packets for each port.
Total Port
Definition: Number of asn ports configured for packet processing.
Limited by hardware capabilities and configuration, typically between 1 and 8.
Control Port
Definition: Designates the asn port used for control plane traffic.
Must select a valid port from available options (e.g., port0, port1)
The following image illustrate the Features and Packet core interface configs such as Radius, metadata export,4G & 5G interface type etc.
Enable Radius
Definition: Enables or disables support for the RADIUS protocol, used for authentication and accounting.
Set to "true" or "false" based on deployment requirements.
Active Bearer Export
Definition: Enables the export of active bearer information for monitoring or analytics.
Uplane Flow Stats (Control Metadata):
. Definition: Enables collection and export of user-plane flow statistics as part of control metadata.
Packet Core Interface:
Definition: Selects the type of packet core interface for network connectivity.
4G Interfaces: S5-S8, S11
5G Interfaces: N11
The following image illustrate the Kafka Producer configs such as Queue buffer, compression type etc.
Queue Buffer Messages (max):
Definition: Maximum number of messages buffered per Kafka queue before sending.
Range is 1,000 to 1,000,000,000.
Queue Buffer kbytes (max):
Definition: Maximum buffer size in kilobytes per Kafka queue.
Range is 1 to 2,147,483,647 kB.
Queue Batch Size (max):
Definition: Maximum number of messages sent in a single Kafka batch.
Range is 1 to 2,147,483,647.
Linger (ms):
Definition: Time in milliseconds to wait before sending a batch to Kafka, allowing more messages to accumulate.
Range is 0 to 900,000 ms.
Compression Type:
Definition: Compression algorithm used for Kafka messages.
Must be one of: none, gzip, lz4, zstd, snappy. Unsupported types will cause errors.
Deep Packet Inspection (DPI) is a powerful technique that analyzes network traffic at the packet level, going beyond basic header inspection to examine the payload of the actual data being transmitted.
Aviz Service Nodes support in-service DPI upgrade for enhanced new DPI library integrations.
The Control Session Timeout Support feature enables automatic handling of inactive control-plane sessions by detecting and cleaning up sessions that exceed a defined period of inactivity.
To configure and manage control session timeout and active communication bandwidth of ASN via the FlowVision GUI, navigate to:
Configuration > ASN > Threshold and Timeout
Threshold and Timeout Configuration Options:
control session timeout
Selecting the control session timeout, you can configure both value by H:M.
KPI Active communication: configure threshold bytes and interval time
Below image show control session timeout and active communication configuration





The configuration menu helps you perform the following:
To configure ASN ports using the FlowVision GUI, navigate to:
Configuration > Ports.
This page displays:
Managed Nodes and their connected ports.
A detailed Ports Table showing:
Admin Status.
Link Status (UP = Green, DOWN = Red).
Speed & Mode.
Port Modes in ASN:
Cplane (Control Plane): Handles control-plane traffic, such as S11, N4, and N11.
Uplane (User Plane): Manages user-plane traffic, including S1-U and N3.
The following image illustrate the ports page with device, ports, and port status details:
Hover over a device or port icon for additional details.
To edit the properties of a port,
Click the Edit button against the required port in the ports table. The Port Properties window displays.
Update the above properties as required.
The following properties can be updated -
Description: Sets a custom link description
Admin Status: Configures the port’s administrative state (Up/Down).
GRE Strip: Enables or disables GRE stripping on incoming packets (applicable only to C-plane ports).
Click Save to apply the changes.
Once the port mode has been successfully changed, the ASN Core will automatically restart on the node to apply the updates
Port Description.


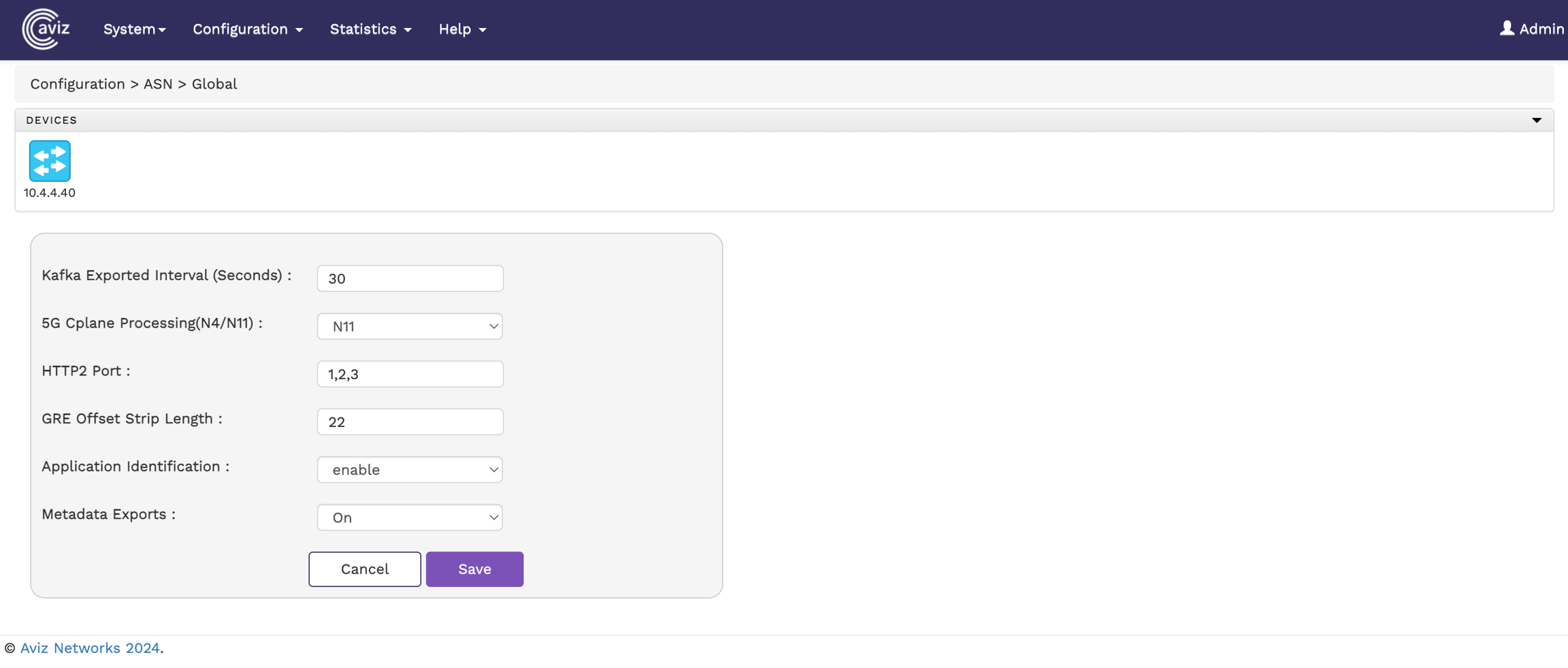
To view and configure ASN global parameters from the FlowVision GUI, navigate to:
Configuration > Global.
The following image illustrates the ASN Global page:
Select a Node to configure the below parameters:
Kafka Export Interval (seconds): Sets the interval for exporting data to Kafka, configurable between 5 to 300 seconds.
5G Cplane Processing (N4/N11): Choose between N4 or N11 for processing 5G control plane traffic.
HTTP2 Port: Define multiple HTTP2 ports, separated by commas (,).
GRE Offset Strip Length: Specifies the length of the GRE header to strip from ingress packets.
Application Identification: Enable or disable application identification.
Metadata Export: Enable or disable data export to Kafka.
Packet deduplication is a feature used to identify and eliminate duplicate network packets, improving network efficiency and reducing redundant data processing. It works by comparing incoming packets
To configure and manage packet deduplication of ASN via the FlowVision GUI, navigate to:
Configuration > ASN > Deduplication
Deduplication Configuration Options:
Packet Deduplication: Toggle this option to enable/disable deduplication.
Selecting the Packet Source, you can choose one of the following packet sources:
Full Packet: Deduplication is applied to the entire packet.
Routed Packet: In real time, the packets can be routed across multiple devices/hops. Hence there are chances the duplicate packets can be received to monitoring fabric with different Src MAC/TTL/Checksum fields.
Anchor : Determines the starting position for packet comparison during deduplication. Available options:
Packet Start – Begins deduplication from the start of the packet.
L3 Start – Uses the Layer 3 (network layer) header as the reference point.
Offset: Define the byte offset from the anchor point where deduplication begins till the provided bytes (14 to 128 bytes)
Window Size: The time interval within which duplicate packets will be identified. Available options: 2,4,6 & 8ms.
Deduplication Interface: Select the network interface where deduplication should be applied.
Below image show packet deduplication for full packet
Below image show the Packet Deduplication for Routed Packet
When the Routed Packet option is selected, users can exclude the following fields from packet deduplication:
Ignore IPv4 TTL: Ignores changes in the TTL (Time-To-Live) field for IPv4 packets.
Ignore L2 Header: Excludes Layer 2 (Ethernet) header fields from deduplication.
Ignore IPv4 Checksum: Ignores differences in IPv4 checksums when comparing packets.
Packet drop for a few milliseconds is expected during configuration changes as the deduplication module reinitializes.
The deduplication feature operates in DC mode.
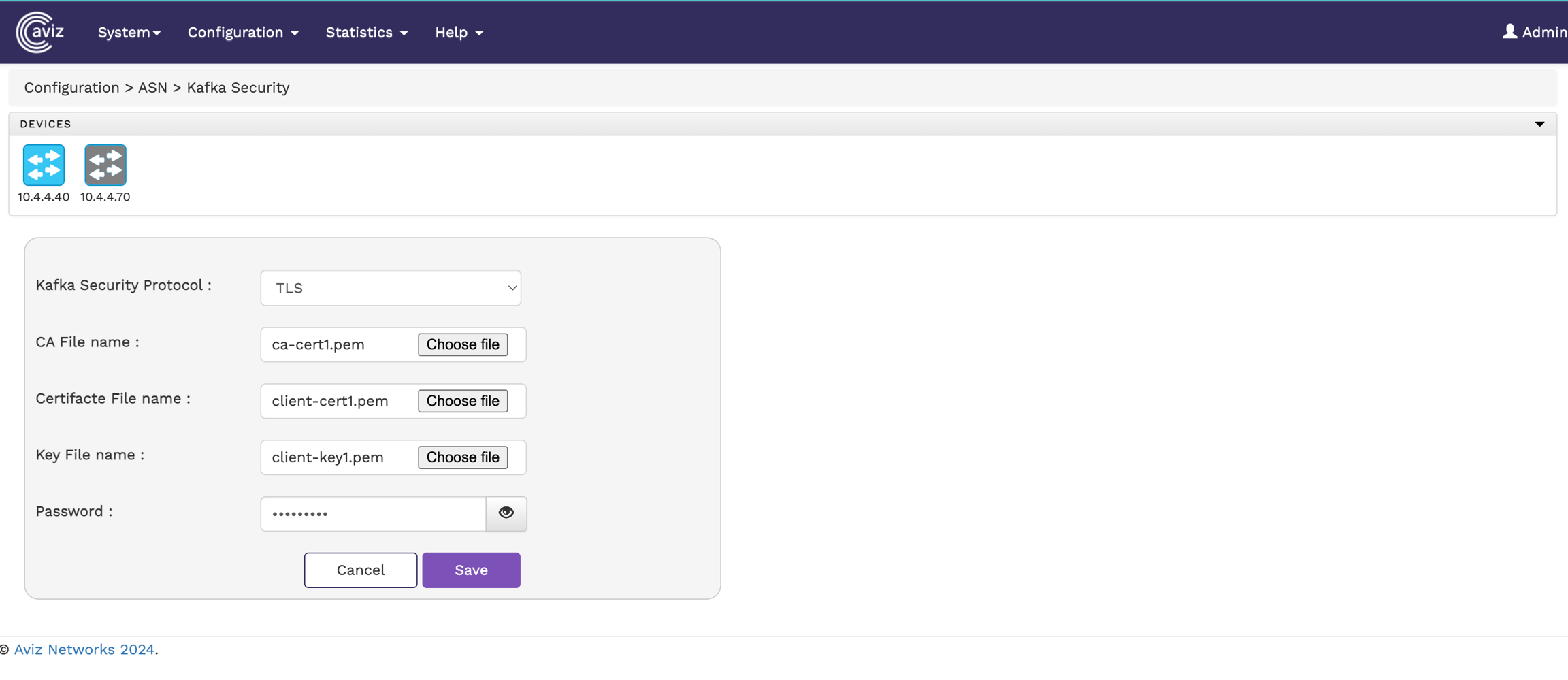
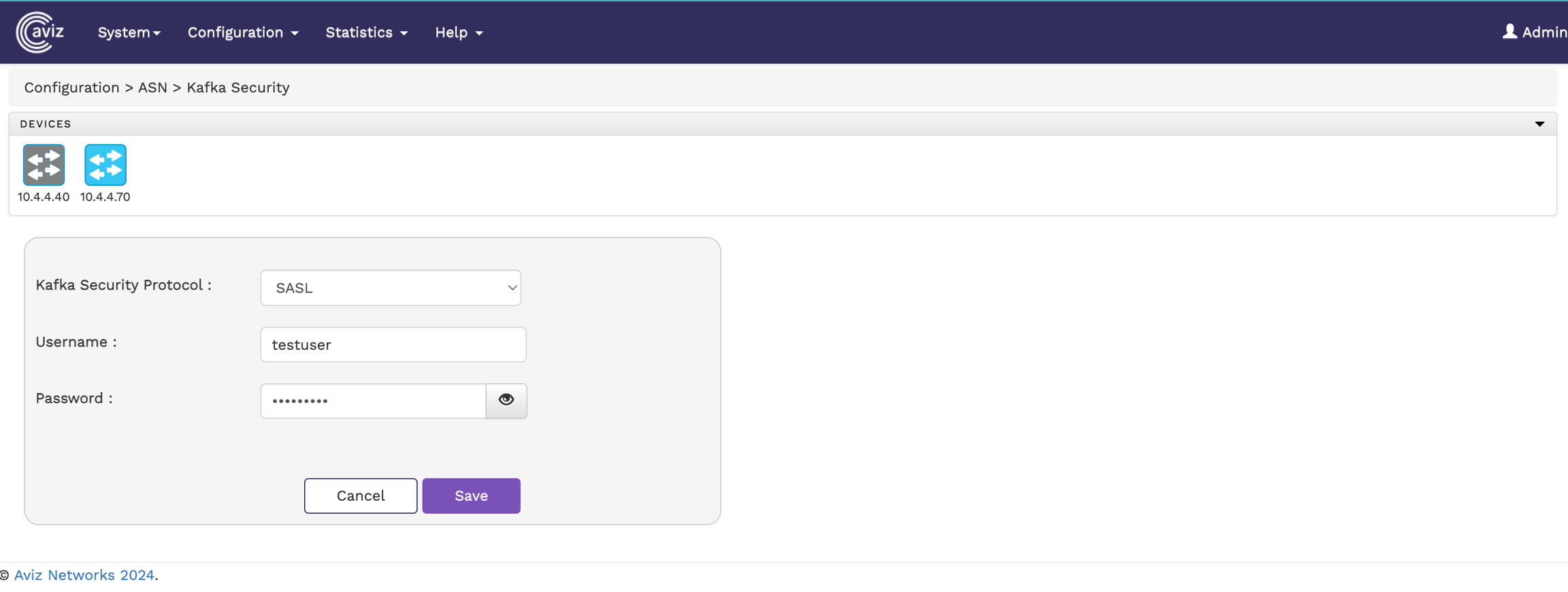
To configure Kafka Security settings in the FlowVision GUI, navigate to:
Configuration > Kafka Security
This page allows you to modify Kafka security protocols and their configurations.
Configure SASL authentication by providing:
Username
Password
Click Save to apply the changes.
To enable TLS security, upload the required files:
CA File
Certificate File
Key File
Below image illustate TLS configuration page
Ensure the correct CA, Certificate, and Key files are uploaded.
Only .pem format files are supported.
If you don't want to configure SASL or TLS security, select "None" here to disable Kafka security.
If a user changes the configuration but clicks Cancel instead of Submit, the system reverts to the previous settings automatically.
Only an Admin can configure or modify Kafka security settings.
L4 Payload – Focuses on the Layer 4 payload for identifying duplicates.



The Packet Capture feature allows users to capture network traffic on selected interfaces for analysis. It provides configurable options to define capture duration, file size limits, & interface.
Accessing Packet Capture
Navigate to Configuration > ASN > Packet Capture.
Select the device for which you want to capture packets.
Configure the capture settings as needed.
Capture Duration (ms): Specifies the duration in milliseconds for which packet capture will run. The value can range from 1 to 10,000 ms..
Capture File Size Limit (MB): Defines the maximum file size for the captured packets before it stops capturing. The value can range from 1 to 1,000 MB.
Capture Interface Config: Allows selecting the interfaces (ports) from which packets will be captured, supporting both received (RX) and transmitted (TX) traffic.
Configure the desired settings.
Click the Start Packet Capture button to begin capturing network traffic.
Below image show the Packet Deduplication for Full Packet
Packet capture will stop on all configured ports if the cumulative file size or capture duration limit is reached on any port.
Captured PCAP files are stored in the ASN server at /var/log/ and can be transferred using the Linux SCP command.
RX/TX File Name: Defines the filenames for received (RX) and transmitted (TX) packets.
Clean Up Old PCAP File: When enabled, previously stored PCAP files will be deleted before capturing new data.